Securely store customer data
Footprint securely vaults three types of data: identity data, payment card data, and custom key-value data.
Confidential computing
Nitro Enclaves provide isolated compute environments that are designed for processing highly sensitive data.
Trusted execution environment
All interactions produce a signature which asserts there has been no tampering to the underlying environment.
Vaulted immediately
When a user goes through the Footprint KYC flow, their data is automatically vaulted.
Built-in permissions
Create unlimited roles to make sure the right people in your org have access to the right data.
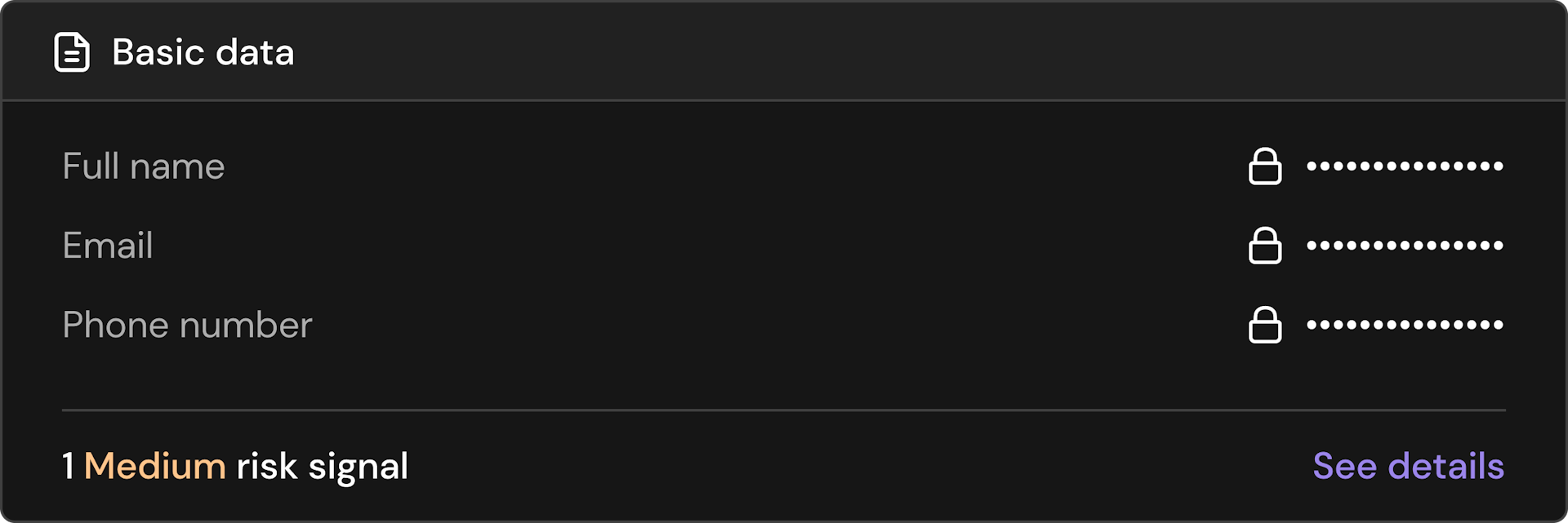
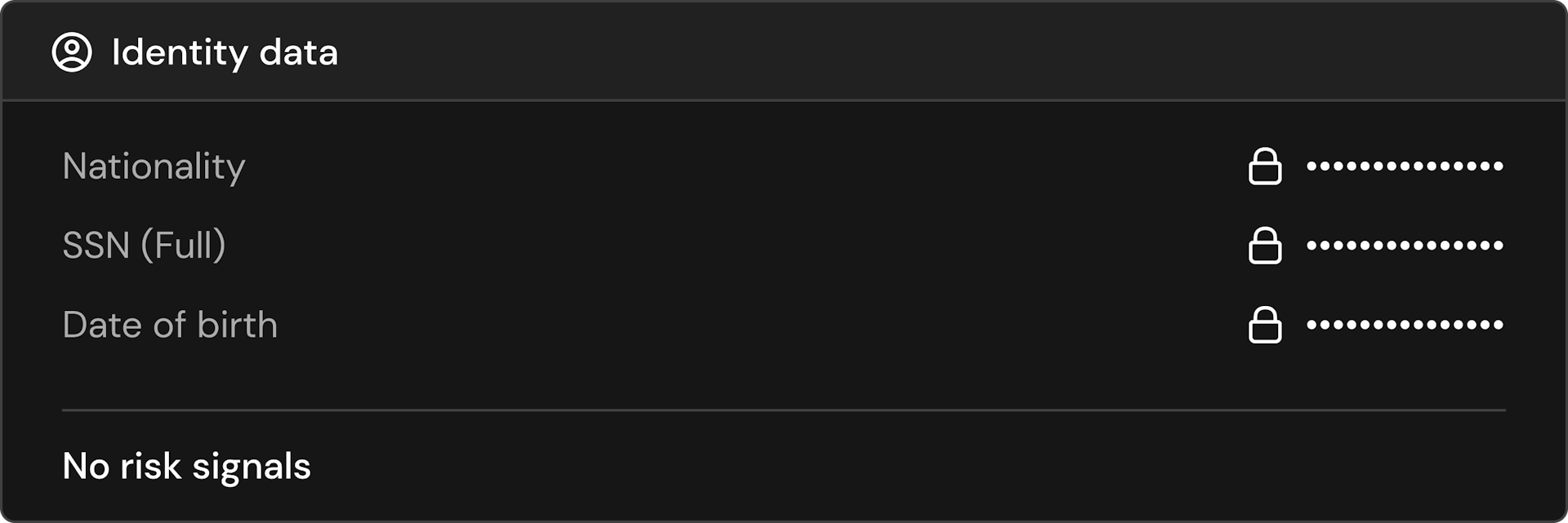
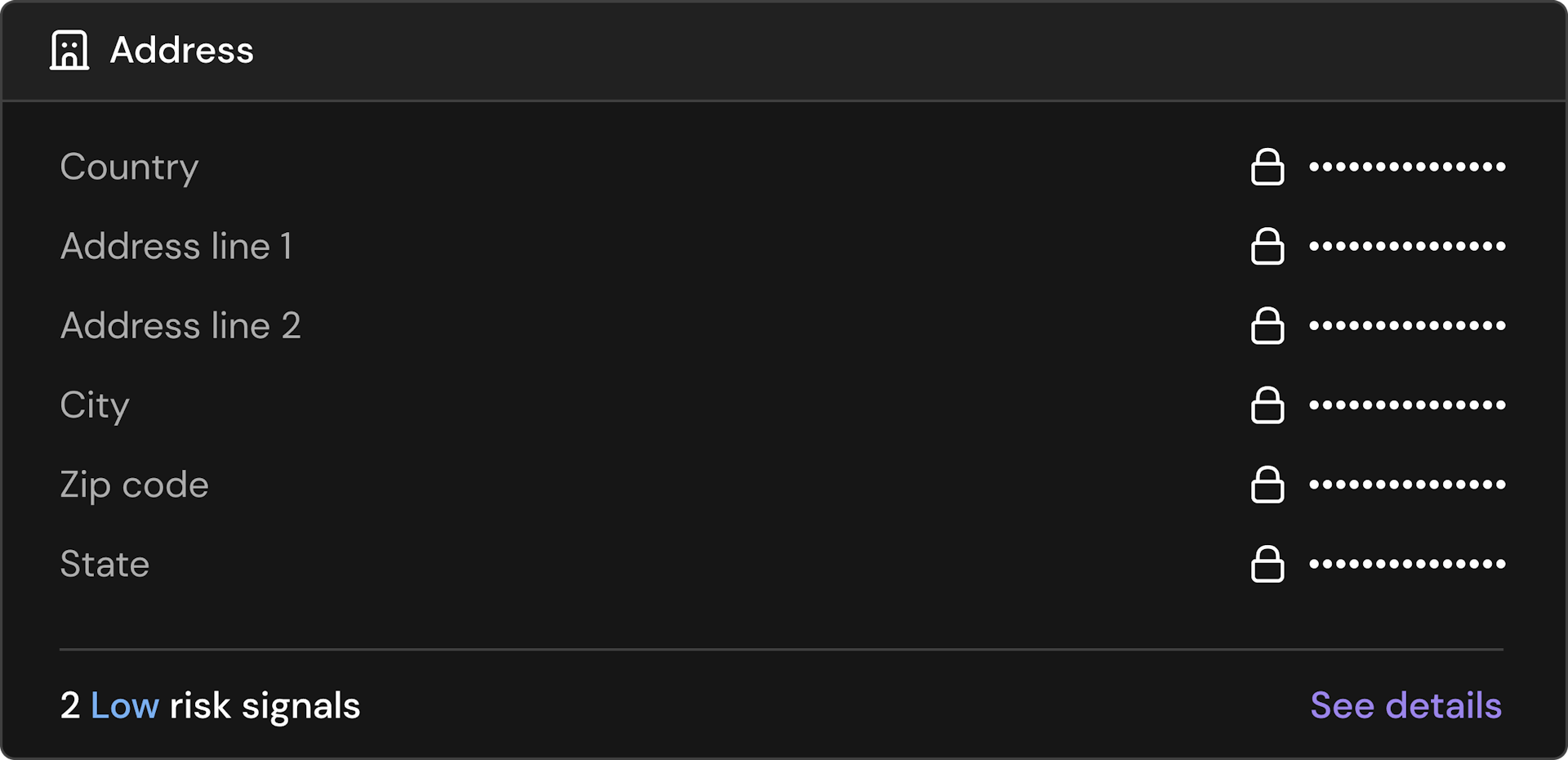
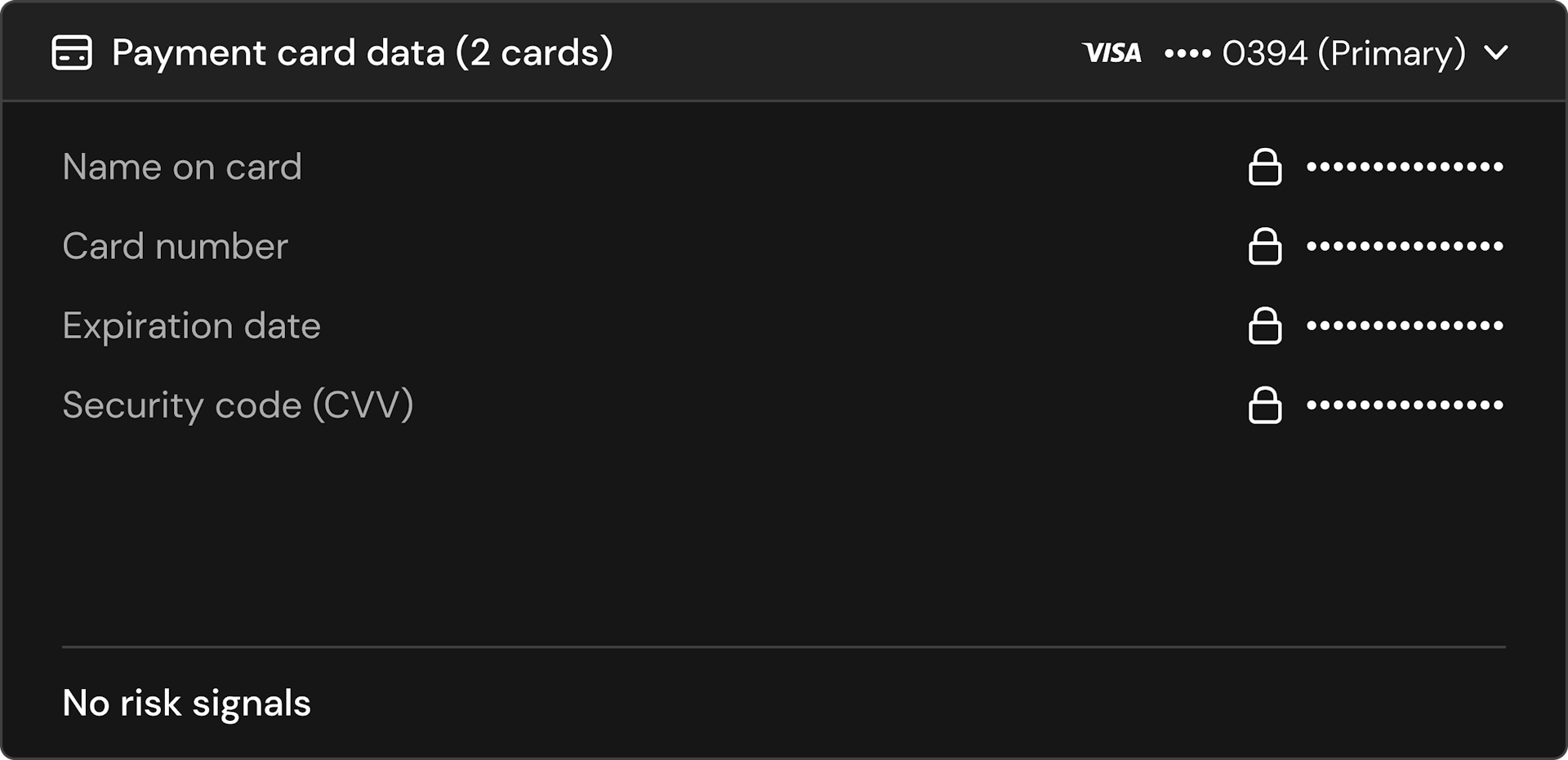
All of your customer data.
The Footprint dashboard brings good security into an intuitive and interactive dashboard.
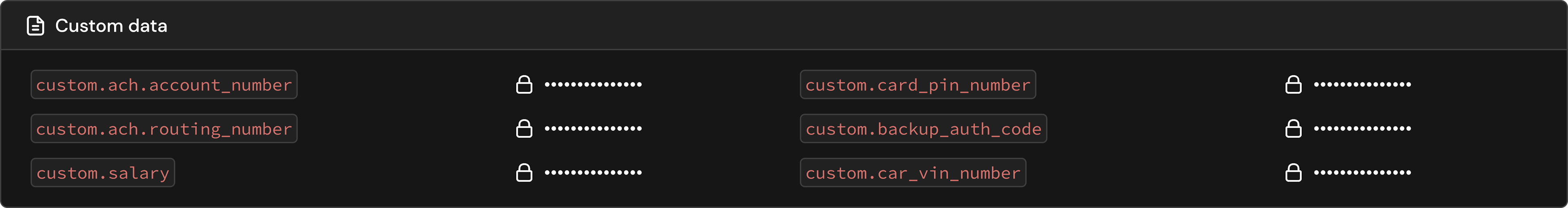





Audit trail timeline
Compliance regimes can export records with a click of a button.


Vault proxy
Send PII data to third parties from Footprint without having to decrypt it yourself.
{{ fp_id_SrdJshjthjSQq.cred_card }}
{{ fp_id_SrdJshjthjSQq.cvv }}
{{ fp_id_SrdJshjthjSQq.exp }}
{{ fp_id_SrdJshjthjSQq.name }}
{{ fp_id_SrdJshjthjSQq.address }}
{{ fp_id_SrdJshjthjSQq.snn }}
1234 1234 1234 1234
123
12/22
John Doe
1234 Main St
123-45-6789

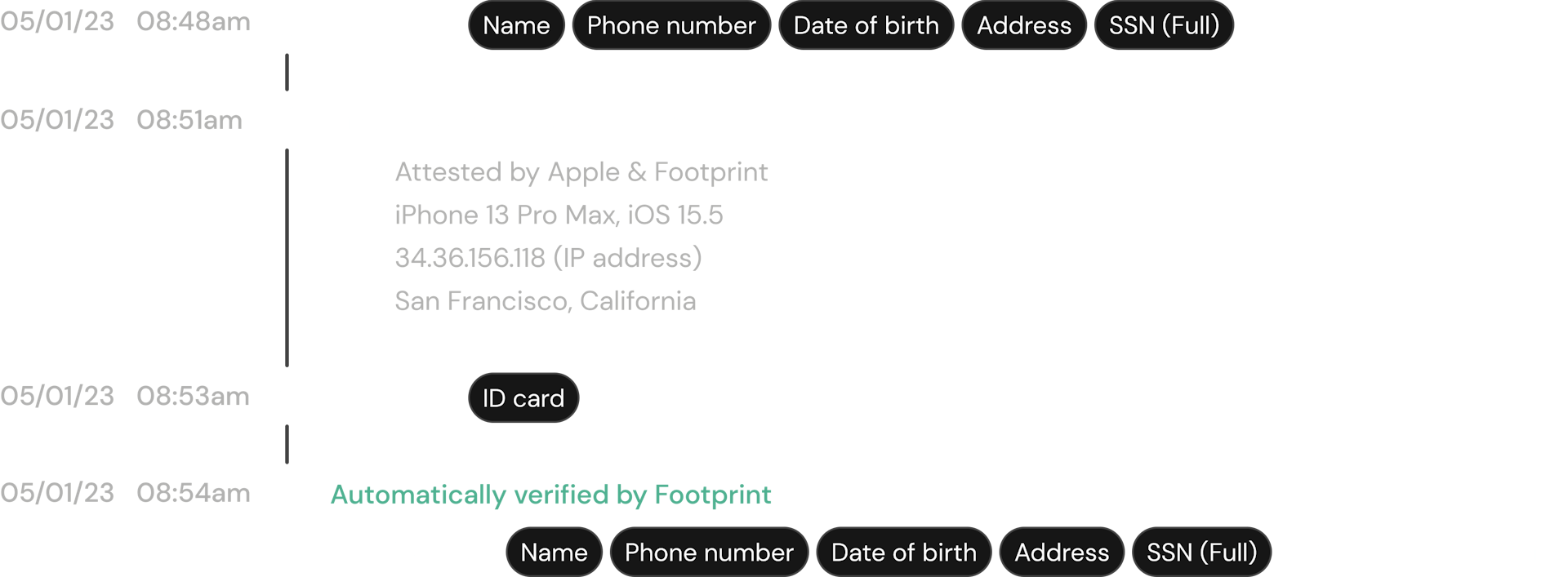
Device insights
Goodbye heuristics. Hello real people.

We've got all the features
See why product, engineering, risk, and security teams live in Footprint.
Manual review
In the event we can't automatically verify a user, you can easily review them yourself and make a pass/fail decision.
Auth & IAM
Identity should not be limited to onboarding. Footprint helps you bridge the identity gap from onboarding to auth to IAM.
Fraud & risk
By tying security to fraud to KYC, we can create a bar to enter the digital ecosystem.
Security logs
Each time data is accessed in, it automatically gets appended in our security logs, which are always accessible via API.
Watchlists
Footprint makes it easy to visualize when watchlist checks were run for continuous monitoring.
KYC retrigger
Sometimes you need to re-run verifications. We make it easy.
Free-form notes
Everyone is different. Understand the decisions you made with custom notes.
Field validations
We make sure the data you collect is valid real time.